- Access Control
- a means for establishing the rights an authenticated party has to access and control a set of resources.
Thanks.
- Access Control List
- A list of people who should have access to some particular information.
This idea is deprecated on these pages.
Butler Lampson’s description
- Address Space
- In Keykos, the segment defined by the key in the address slot of a domain.
- Allocation Count
- Internal Keykos kernel feature
- Ambient Authority
-
The implicit unnamed authority that a program uses in typical system calls.
When a program uses a text stream as the name of a file that it reads, it has used its ambient authority to read any file in that directory.
- Amplification
- See Rights Amplification.
- Apartment
- A general term for an area within a machine where a guest program,
with its own interests, can privately prepare to interact with other interests on the same machine.
Apartments come in a variety of forms with various security properties protecting both host and guest.
Mentioned here and here.
- Attack Surface
- Code that interprets messages from untrusted sources.
Such messages may be crafted to confuse the code and cause it to abuse its authority to the benefit of sender of the message.
It is a development cost and execution time penalty to test incoming messages for conformance to expectations.
When the sender is trusted this code is frequently omitted.
This omission is seldom documented.
- Attenuation
- A capability pattern: An object O holds a powerful capability P.
Few other objects hold P.
O’s defining code invokes P only in a very restricted way, such as with some particular parameter value or with just two different order codes (methods).
Capabilities to invoke O are more widely spread than P.
P is hereby attenuated for an expanded set of users.
- Attestation
- Some platforms propose to have the ability to digitally sign a message attesting to some remote agent that some particular configuration of code has been instantiated.
The configuration is identified in the attestation by a secure hash of the configuration.
This configuration presumably has the property that the state that the code will bring about will be veiled.
See this.
- Authentication
- The strong identification of a source of information or instructions.
Elsewhere this commonly means identifying a person.
On these pages it more often means identifying a computing object, often remote, perhaps to the end of identifying a person.
For example a Message Authentication Code (MAC) is extra information in a packet used to assure that the rest of the packet came, unaltered, from the expected source.
- Authority
- “Authority” used here describes what a program can do thru direct and indirect means as a consequence of how it is situated within the system.
This is to be contrasted with permissions which prescribe the immediate actions a program can take.
It is also somewhat at variance with some computer security usage where it is taken as a policy which is the goal of the computer platform security mechanisms.
It is thus opposed to a common normative English meaning of what the correct program, by rights, should not go beyond.
We characterize the authority of a program as the set of effects that it is able to have and the sources of information it is able to use.
In the context of operating systems we say that a program has the authority to do something if some pattern of bits in the machine language code stream of that program would make it do that thing.
In other words operating systems don’t concern themselves with the patterns of bits that are executed in user mode, in order to achieve their security.
In contrast, Java JIT compilers achieve their security properties by constructing disciplined application code.
Note that we seldom need to distinguish between the immediate effects that a program can have (in a single system invocation) from the larger set of effects that result from a sequence of actions.
In a capability system the authority of a program stems from just those capabilities that it holds.
In a Java program it is the object references that it holds (some equivocation here!).
In other systems it is more diffuse.
- Availability
- ensuring that system resources such as data and servers are up and running when needed.
Security breaches can compromise availability; e.g. “denial of service” attacks.
Thanks.
- backchain
- Internal Keykos kernel Jargon: Real keys to the same thing in RAM are connected via a bilateral chain rooted in the thing designated.
- Behavior
-
The rules that govern the state transitions of an object.
In Keykos behavior of an object implemented by a domain, is defined by the code that the domain executes.
See “state”.
- Brand
- Property of a Keykos object that conveys membership to a class like concept.
- Cahoots
- For X to be in cahoots with Y means that X and Y work together in support of some mutual end.
In Keykos this usually means that two different objects cooperate to secure some abstraction, whereas usually such abstractions are achieved by just one object.
- Capability
-
A protected pointer or name, implemented with bits but situated so that the holder and user lacks access to those bits.
Capabilities may be passed among programs but only by means of protocols that specifically allow capabilities to be passed, as they are not data.
In a capability system:
- For a program to access an object it is necessary and sufficient for that program to hold and designate a capability to that object.
- The capability is the only system mechanism used to name or locate user or system components within the system.
Thus to employ the authority of a capability, the program must designate that capability as it employs its authority.
Here is Jonathan Shapiro’s introduction to capabilities.
- CDA
- Coded Disk Address, an internal Keykos kernel construct.
- Channel
- An archaic term used to describe autonomous hardware that obeys a sequence of “channel commands” to move blocks of data between a computer’s memory and IO devices.
The channel interprets the commands, signals the IO device and moves the data.
Channels (at least by that name) perhaps arose first on the IBM 709 in 1958 and continue today by that name in the IBM 390 as well as other big iron.
A channel includes the function of modern DMA.
- Checkpoint
- To capture the current state of processes within a system.
See Persistent.
- Client
- When an object A holds and invokes a capability to object B we say that A is a client of B.
We also say that B is a server and that A is one of its clients.
- c-list
- Capability systems in good standing assign to each domain, process or protection domain, some sort of array of capabilities often called a “c-list”.
Code that uses such capabilities identifies them by providing the index into this array.
The 16 slots in the general keys node of a Keykos domain constitute that domain’s c-list.
- Closely Held
- Said of a capability or a class of capabilities;
but typically one of a kind, such as the domain tool.
Closely held keys are designed to be held by some small fixed set of programs in order, typically, to insure the safety of the entire system.
- Compartment
- Their purpose is to run software where the permissive Microsoft style of “any one can do anything to anybody” has been found useful.
The compartment places limitations on “anybody”.
- Concurrency
- Simultaneous progress on a task by multiple agents which is at least for intervals of time, uncoordinated.
Dean Tribble proposes that “concurrency” in contrast to “parallelism” q.v.,
describes situations where these several sites of progress are for logical rather than performance reasons.
For instance there may be two tasks, of which one is sure to fail and you don’t know which.
You must not wait to start the second until the first finishes.
- Confidentiality
- a policy ensuring that information is kept private and therefore seen and accessed only by authorized user.
Thanks.
- Confinement — Confine
-
Limiting code from sending data that it can access to places and code that should not be able to access that data.
The Factory description has some pointers to further ideas on confinement.
Here are some observations on distributed confinement.
This discusses confinement of applet style code.
Some similar terms contrasted.
- Confused Deputy
- Some programs run with authority from multiple sources.
Correct programs must usually specify the source of any authority they wield.
A deputy is confused when it has no means of doing so.
- Continuation
- A concept invented along with the subroutine, but unnamed then.
The continuation is the system’s record of what to do after the code in the subroutine has finished.
The continuation is usually embodied in the stack.
The continuation is explicitly accessible in Scheme and introduced here in the language definition.
If the routine is to produce a value then the continuation is waiting for that value to proceed.
Even when no value is returned the continuation may need to wait until the actions of the subroutine have been performed.
The Keykos resume key provides access to a continuation.
A nexus for continuations at this site.
- Covert Channel
- A system property not meant to convey information that can be used to copy information from one program to another.
e.g.
This may be information flow that is not limited by security policies.
These may thwart confinement.
Butler Lampson enumerates many in his Confinement Problem paper.
The NCSC considers covert channels extensively.
- CORBA
- A standard conceptual interface between object systems.
As such it provides a framework for distributed capabilities.
- Data Abstraction
- Data abstraction is what keeps the caller of a procedure from accessing data that the procedure manipulates.
Algol60’s own variables provided a special form of this.
Private instance variables in OO languages provide a more general form.
- Data Byte
- Some constant data in a Keykos key delivered to the code defining the key.
Called badge in other systems.
- Defend
- said of an environment which protects its contents from unmediated modification by external actors.
- Defensive Consistency
- Property of a server whose behavior towards one client cannot be corrupted by the behavior of another client.
The term was introduced by Mark Miller in section 5.5 of his thesis.
- Denial of Service
- An attack on a system or portion of a system that results in at least the temporary inability of others to use the system for its intended purpose.
Such attacks do not directly destroy or steal data.
- Discreet — Discretion
- An object or complex is said to be discreet when the ways it has to export information are limited to a known (often empty) set.
Factories produce discreet objects.
Also Distributed yet Confined.
- Dispatcher
- A mechanism to select a currently available domain to process a new request
- Distributed
- As used in the pages at this site, application code whose components run within separate systems whose communications are limited to primitive messages holding data but no capabilities.
We discuss techniques here, using code that is itself subject to capability discipline, which effectively transmit capabilities in this case.
- Domain
- Briefly domains are the Keykos objects that obey the native machine instructions in a Keykos system.
CapROS has much the same construct that they call a process.
- Domain Tool
- The small ultimate class like function of the Keykos kernel.
- Dry Run
- A Keykos kernel lock discipline
- Durability
-
An object, or complex of objects is durable if it is known to be invulnerable except to a known set of sources.
- E
- A language that embodies capability ideas.
- Exfiltrate
- Making a copy of nominally protected data to someplace outside control of the protection regime.
A useful new buzzword in CS to describe what confinement prevents.
Exfiltration does not imply modification of the data left behind.
An extra goal of exfiltration is usually to avoid leaving evidence of exfiltration.
- Extensible Capability System
- A capability system in which objects of newly defined behavior can be introduced by adding user mode code which is itself constrained by capability logic.
- Facet
- A term from Joule.
There may be several facets to an object.
They convey different authority.
I may own an object and all of its facets.
I may choose to pass one of those facets to you whereby you can invoke the methods (OO speak) or orders (KK speak) peculiar to that facet.
I have more authority over the object because I have more facets.
In Keykos there might be (1) node keys, (2) domain keys or (3) start keys, to the same node.
These are like three facets to the same object.
Start keys with various data bytes provide the principle form of facets in Keykos.
If the OB foundations do not provide facets the effect may be produced by intermediaries which limit the messages to the object.
Java and C++ do not provide facets.
Thinning makes a special sort of facet.
- Factory
-
A type of object in Keykos that produces discreet objects (q.v.).
- Fork
- In the context of Keykos, a transitive verb.
When domain A forks domain B, a message is transferred from A to B and both domains are thereafter running.
- Fort
- A source of environments into which the flow of signals is controlled.
Forts provide durability as factories provide discretion.
- Gate key
- A key which designates a domain and restricts the holder to invoking the
domain and sending a message to be interpreted by the domain code of the domain.
Gate keys are either start keys or resume keys. All keys are either gate keys or
primary keys.
- Granovetter Diagram
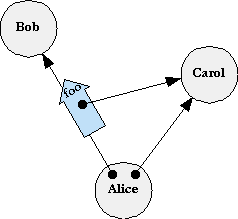 Introduction
Introduction
A diagram emphasizing that it takes a capability to convey a capability.
- Gullible
- Used in these pages to describe software that may obey instructions from unauthorized sources.
It uses its authority gullibly.
In ordinary usage a “gullible” person tends to believe statements regardless of their source.
- Hole
- In the context of factories a hole is a key that decreases the discretion of the yield of that factory.
See factory theory.
- Immutable
- An object is immutable if its response to signals (invocations) is a function of the signal and does not depend, for instance, on previous signals or the phase of the moon etc.
In KeyKos, a page to which there are no read-write keys is immutable.
So is a factory, by virtue of the factory code.
An immutable object may be deleted whereas there may be limits on the deletion of durable objects.
- Impervious
- A proposed name for the state of a domain to which there are restart style resume keys.
- Integrity
- An aspect of security.
Vaguely, integrity means the steps taken to preserve some state of affairs.
We might say that a computing infrastructure supports integrity if it protects application programs running therein from interference.
Perhaps the only signals allowed from outside are delivered so that the application code may interpret them so as to be effected by those signals only as it chooses.
The application can thus sense the outside world while preserving its inner structures.
In the extreme the execution of an application is predetermined by its official input.
Systems have been built that achieve this extreme.
Durability is an attribute of some immutable objects and entails integrity.
An application is seldom immutable but the factory from which applications come may be to a degree, durable.
Julia Bort defines integrity thus:
| a property ensuring that information transmitted on a communications channel is identical to the information received via that channel, without alteration en route |
I would use authentication (q.v.) for this but they are close.
“Platform Stability” might serve in place of my “Integrity”.
- Invoke
- To invoke a capability, is to send a message while specifying that capability to define the recipient.
The capability designates the recipient.
To invoke an object and to call it usually mean just the same thing.
- Isolated
- Said of an environment that prevents incoming signals even as mediated by programs in the environment.
- Joule
- A language that embodies capability ideas.
- Key
- In the Keykos literature “key” refers to what is elsewhere called a capability.
In more general security contexts “key” is more likely to refer to a cryptographic entity—secret data that enables encrypting, decrypting, signing or verifying a signature.
- Keeper
- A program designed to react to unusual circumstances.
The general idea is to simplify primitive objects by allowing externally specified policies in the form of keepers.
Capability architectures allow keepers to wield just the authority that they should.
Developed especially in Keykos and generally described here.
- Kernel
- The part of Keykos (or other OS) that runs in privileged mode.
Synonymous with “microkenel”.
Keykos kernel
- Keykos
- An operating system built in the 80’s around capability ideas.
- Mandatory Security
- Officially when A (perhaps a security officer) arranges that B can’t send data to C, instead of leaving that decision up to B.
See this observation, however.
- Membrane
- A pattern that spawns a compartment; I quote from here:
For the uncooperative case, we’d have to use a different pattern that’s been referred to on e-lang by various names, including “membrane” or “compartment”.
Just as our above forwarder is a “Man in the Middle” (MITM) between our client and the capableObject, a membrane starts in the middle, but then looks at all messages going in either direction and wraps all the capabilities in a new membrane-forwarder, thereby extending the membrane as the surface area of capableObject and the objects gotten from it grows.
but the ANNALIST was implemented in 1988.
The Annalist is discussed here.
High density note
- Meter
-
A primitive Keykos mechanism to deliver and measure CPU time.
Also Keykos may provide unique means for measuring access to proprietary data.
- Multics
- A pioneering operating system built in the late 60’s and early 70’s.
Not capability based but still the source of many Keykos ideas.
- Mutually trusted
-
For a pair of mutually suspicious agents X and Y, within a computer system “mutually trusted” refers to some other agent within the system that is in the intersection of the TCBs of X and Y.
- NCSC
- The National Computer Security Center.
- Node
- In Keykos a node is a persistent block of storage which comprises 16 slots.
Nodes never appear in the address space of user mode programs in Keykos.
Their semantics are defined by kernel code.
- Nonrepudiation
- The ability to ensure that parties cannot deny their electronic actions.
Thanks.
- Obey
- Originally a British term for what a CPU does with a program while the CPU is running.
Some say that the computer “executes” the program but that suggests, falsely, that the computer decides what to do.
“Performs” would do nicely but “obey” is even shorter.
- Object
-
A bundle of behavior and state.
Some objects are primitive and defined by code that is not subject to capability discipline, while other objects are defined by code that need not be widely trusted because it is confined by capability discipline.
- Parallelism
- When a task is partitioned into parts so that multiple pieces of hardware can be used to get the answer sooner.
The pieces usually are cpus but IO channels may also provide headway towards a goal.
See “Concurrency” by contrast.
- Password
-
Everyone knows what a password is.
It is some information that you can say or type to convince someone or something that you ought to be allowed to do something.
A password is not a capability because it is not protected.
Also a capability locates something whereas a password does not.
- Permissions
-
Categories of direct actions that are allowed to a program by the platform upon which it runs.
This is opposed to “authority” which includes indirect actions.
- Persistent
-
A system is persistent if the state of all programs is automatically preserved across power off.
Keykos achieves this with normal hardware and checkpoint-restart logic.
In persistent systems, such as Keykos, ordinary program variables may retain their values for the lifetime of a physical machine or longer.
- (Computing) Platform
-
An emerging category of technologies which include operating system kernels and various other arrangements for software to work together.
A platform hosts multiple applications and sets rules on how they may communicate with each other and the external world.
The Java Virtual Machine (JVM) and Common Language Runtime (CLR) are prominent platforms.
On these pages we preach that platforms should impose capability security.
- Police
- Typically an object P is implemented by holding authority that it does not yield to its clients.
Most of these are capabilities to private parts of P.
Sometimes P holds a capability to some shared object that is not private to P.
P may be responsible for limiting the use of the shared object.
I call this a police function.
This policy may be to limit what the P’s client can learn from the shared object, or to limit what the client can do to the shared object.
Often both.
Sometimes the sole function of P is to attenuate the authority over the shared object.
This might be called a front end.
- Polyinstantiation
- Alternate states of affairs reported within one system.
- Primitive
- We say that an object B is more primitive than another object A when the implementation of A involves instances of B.
The implementation techniques that we use require the relation “more primitive than” to be a partial ordering.
When referring to a primitive object we mean that no other objects are more primitive.
Primitive Keykos objects are implemented in the kernel.
- Principal
- Person on whose behalf a program acts.
This site deprecates the idea that the acts of a program are necessarily compatible with the intent of the person classically identified as the principal.
- Privacy
-
Roughly the ability of a person to limit what computers that know about him can say about him to other people and computers.
There is not much on this site about this difficult problem.
Here is a good discussion.
- Privilege
- Privilege is much like authority but consists of the effects a program can directly have within the system.
A program can increase its privilege by fetching a new capability but it cannot increase its authority.
- Privileged Code
- This is code designed to run while the CPU is in privileged mode.
Such code usually has as much authority as any code within the machine.
See user code by contrast.
- Privileged mode
- A CPU state in which privileged commands are obeyed.
Such commands affect the entire state of the machine and their abuse can corrupt the entire system.
- Problem Mode
- An IBM term for the alternative to “Privileged mode”.
- Process
- The meaning of this word has shifted greatly since 1965.
Much Keykos documentation uses the old meanings.
- Old meaning:
-
By “process” Multics meant about what “thread” means today in Unix.
Another name for this concept is “locus of control”.
Concretely a process includes a register values for each of the program visible registers and perhaps some of the invisible registers as well.
A process is what a scheduler might allocate a processor (CPU) to.
Sometimes the activity of a channel is referred to as a process.
In this case the channel is the processor (not a CPU).
A channel is approximately the same as a DMA; it causes sequentially dependent IO actions to happen independently of CPUs.
It uses a script stored in RAM sometimes called a “channel program” just as a CPU obeys a program.
In Keykos a domain has zero or one processes occupying it.
There is a process in a running domain but not in a waiting or ready domain.
- New meaning:
- In Unix “Process” is a construct comprising an address space and several other smaller constructs.
Several threads and thus several processors may be executing at once in a Unix process.
A Unix process has a set of environment variable values; a name space.
A Unix process has a name space consisting of environment variables and their values.
It has a GID and UID that directly and indirectly influence what actions the threads can take.
Nothing in the Keykos kernel packages the Unix process functions.
- Protection Domain
- The protection domain is a subset of the software, and its data, that runs on some platform.
Properly crafted code with a protection domain all to itself can ensure its own integrity and behavior, subject to the platform maintaining its own integrity.
Only a few platform designs can provide suitable protection domains and there is much controversy over precise meanings; there is, however a broad consensus.
One of the controversies is how protection domains should arise and be able to interact.
The Keykos domain is a protection domain in this sense and constitutes what I see as the ideal protection domain.
Some languages support patterns wherein program constructs can achieve the purposes of protection domains by relying on scoping rules and such.
- Prompt
- In Keykos, said of a key whose invocation was known to produce a response promptly.
No signals from outside the machine are necessary to complete a prompt transaction.
- Protected
-
Said of a capability when either:
- knowing the bits of a capability does not suffice to invoke the capability
- holding a capability does not reveal its bits.
I like systems that protect in both senses.
Sometimes the first is traded off for other valuable properties.
- Rabbit
- An informal term for a designed and documented but unimplemented feature of some system, such as Keykos, reserving an architectural niche and thus guiding other designs.
To be implemented if and when the demand becomes real—thus to ‘pull a rabbit out of the hat’.
- Realm
- A vague reference to a portion of a system into which or out of which there is concern about the flow of information or damaging signals.
Realms are mostly one of the four types defined here.
Apartments and Compartments (qqv.) are special cases of realms.
- Red Segment Node
- An artifact in the Keykos memory tree architecture used to indirect calls on capabilities.
- Reliance set
- When we say that a capability platform has some property, it is always relative to some set of objects whose defining code must perform as designed.
The reliance set is that set of code.
The reliance set is about the same as a TCB but depends on what property is under discussion.
Any application generally relies for its security on other software on the platform.
It relies on a larger set for its correctness.
Most platforms have some bottom software called a kernel which is in every reliance set.
- Rescind
- To cancel a capability.
Possible with preplanning.
- Resource
- At this web site “resource” denotes some useful thing that is exhaustible.
The main examples of this are space and time.
(While more time always seems to be created, the time on a particular processor before the year 2000, is an exhaustible resource.)
The patent at this site uses the term more generally.
Resources are allocated in hunks which are usually indistinguishable from other hunks of the same resource and of the same size.
The ability of unprivileged programs to read the real time clock on the IBM 370 means that different hunks of time may be distinguished by the program.
Resources are usually exclusive access, for a time, to some useful hardware.
- Revoke, revocation
- About the same as rescind
- Rights Amplification
- Some service may be able, for some particular set of objects, to exchange a capability to one of those objects, for a stronger capability to the same object.
This is a special case of synergy.
- Seal, sealer, unsealer
- A form of synergy.
Much like public key crypto where a sealer unsealer pair can respectively put a value in a box that can be passed about but only the matching unsealer can retrieve the value from the box.
- Secrecy
- An infrastructure may or may not allow an application to protect its internal state from observation.
An application will typically need to emit signals, but it should not emit any signals to any place except those designed into the application logic.
Technologies to debug an applications must be brought into conformance with secrecy principles.
- Security
- This is an over broad term.
There are many system attributes that have been called “security”.
Among those of interest to software and hardware design are:
Secrecy,
Confinement,
Integrity,
Durability and Privacy.
These have in common limitation of the flow of signals.
In computer security there are general disciplines for arranging various kinds of security short of relying on all of the code in the computer doing what is “expected” of it.
The material in this directory addresses such disciplines.
- Segment
- In Keykos, a kernel construct that defines a span of virtual addresses.
- Sensory
- Keykos speaks of sensory keys that have the flavor of “read-only”.
Sensory keys are capabilities that can be warranted by the fundamental capability mechanism as being unable to produce side-effects.
In Keykos there is the sense key which is sensory and whose invocation fetches a capability and simultaneously weakens it so as to become sensory.
Here is more and yet more on sensory keys.
Also see a proposal for sensory Scheme objects.
- Server
- See client
- Sibling
- Two objects are said to be siblings when they have the same behavior.
Siblings are usually defined by the same code.
Usually the term is limited to those situations where there is a quick proof that the two have the same behavior.
Objects are often permitted to directly access their sibling’s state, as that reveals no secrets and may be more efficient.
This magic is generally brought about by Synergy mechanisms.
- Slot
-
A cell which holds a capability or key.
It may hold different capabilities at different times.
In Keykos slots come 16 per node.
- State
- The current situation of an object as far as it is possible for it to affect the responses that the object will produce in the future.
We can reason about the state and behavior of an object.
Sometimes the division between state and behavior is flexible in that one description of an object may attribute to state what another equally valid description attributes to behavior.
Ordinarily the behavior of an object is determined by the program that it obeys while the state is determined by values of its internal variables.
An immutable object may be said to have no state.
- Synergy
- Sometimes there are actions that can be performed contingent on having, and bringing together, two capabilities.
This is synergy.
- Tamper Resistance
- Most computer systems allow the operator of the system to introduce new code, such as an operating system, that controls the system hardware at the most basic level.
Other computer systems attempt to resist such introduction to some degree so as to insure security properties of the hardware and its data.
These steps lead to some degree of tamper resistance.
See A Cautionary Note for much background.
“Tamper proof” refers to ideally perfect tamper resistance.
- TCB
- Trusted Computer Base.
We speak of the TCB of an application or suite of applications.
It is all that hardware and software outside the applications proper, whose correct operation is relied upon for the security properties claimed for that application.
“TCB” arose in the military computer security community where it referred to those parts of hardware and software that provided the particular security
properties necessary to protect the interests of the military proper.
In these pages we consider systems with distinct overlapping TCBs that protect the distinct interests of distinct parties.
- Trust
- A relationship which allows two entities to cooperate effectively.
I prefer to distinguish between “trusted” and “trustworthy”.
- Tempest
- For our purposes it is the signals that computers send out as a side effect of computing.
The FCC requires that such signals be small in order to avoid interference with other equipment but computers may yet emit radiation that a well equipped adversary can use to acquire data that the hardware and software had not planned to be available outside the confines of the system.
Perhaps CRTs are the most vulnerable.
- Thinning
- Capability Y is a ‘thinned’ version of capability X just if any message to Y is either rejected or has the same effect as the same message to X.
Perhaps this was introduced here.
A common pattern is to address a message to X, asking for Y.
Often of two different facets to the same object, one is a thinned version of the other.
- Type of Key
- Information in the real key used by the Keykos kernel to distinguish between the 17 (or so) types of key between which the kernel distinguishes.
This information is only partially available to user code.
- Undo Pitfall
- A word processing application holds more information than it will print when asked to print.
It holds the information necessary to perform the “Undo” function.
Sometimes it is able to perform multiple undos.
The pitfall is to undo the insertion of controversial text and send the processing document.
The recipient receives that document and performs undo as the first step.
He sees what you thought that you had deleted.
This is a computer security problem for which I know no fix.
The following problems can be overcome by careful programming.
It is not clear how to test for them.
Very similar problems arise if the application writes unallocated storage into a file.
Data may be included that is even inaccessible to the Undo function.
Some file writes at the end of a file round up to a block using whatever data was found in RAM.
Perhaps this problem was first reported here.
- User
- Some agent outside the machine, usually a person, on whose behalf the machine is working and who at least occasionally interacts with the machine.
There are many users to a timeshared system.
Other people who are not users may have proprietary interests that the system architecture is designed to protect as well.
- User code
- In contrast to privileged code, user code designed to be obeyed by a CPU which is in ‘user’ mode or ‘non-privileged’ mode.
It includes no privileged instructions.
Such code must normally be designed with a particular OS design in mind.
- User Replaceable
- System function that can be replaced for some particular application.
- Veiled
- Said of an environment that prevents examination by external actors.
- Virtual
- In these pages, “virtual” is an adjective applied to the name of some relatively primitive construct.
The virtual construct behaves towards its users like the corresponding real construct, but has important additional properties invisible to them.
(The users are programs!)
- Virtual Address
- In these pages “virtual address” usually refers to the addresses that an untrusted program can generate and use—one address space per protection domain.
Unix, Windows and Keykos use this idea.
There are other contexts which use ‘system’ or ‘global’ virtual addresses where protection mechanisms somehow selectively limit virtual addresses from untrusted programs.
- VPN
- Virtual Private Network
A technology to extend the perimeter of a private network to remote locals using encrypted circuits.
This site has nothing to add to these ideas.
- Vulnerability
- In the context of forts a Vulnerability is a key that decreases the durability of the yield of that fort.
See fort theory.
- Wall banging
- wall banging is where two conniving program attempt to transfer information, from one to the other,
contrary to the information flow policies of the computing platform.
Techniques to accomplish this are called covert channels.
- Wrapper
-
Modern OO jargon for an object
that delegates most of the work to another object (the wrappee) that the wrapper object is said to wrap.
The wrapper may present additional or diminished authority to its clients over that of the wrappee.
It may present the same authority by transforming the input or output.
Some wrappers may hold an exclusive capability to the wrappee;
others may not.
This makes a difference if the wrappee is mutable.
The term “front end” is used in these pages to mean the same thing.
 Introduction
Introduction