[Home] [Agorics Technologies] [Tech Library]
Copyright © 2001-2002 Agorics, Inc.
For most corporate Information Technology managers, CIOs, and executives, the lack of information security is a pre-eminent issue. Current industry measures address these concerns by providing selected Authentication and Authorization technology. Much attention has been directed to these technologies (e.g. firewalls or PKI certificates), but they have neither blocked nor slowed sweeping attacks on commerce systems. According to a 2000 Global Security Study conducted by InformationWeek Research and PriceWaterhouseCoopers, 71 percent of executives, IT managers and security professionals surveyed ranked information security as a high priority for business. Reports of security breaches come close to epidemic levels, but only a small percentage of attacks on sensitive information through Internet access become public. Today, sophisticated hackers can gain access to almost any system; only a fundamentally deepened approach can defeat the invasions. "As organizations move more of their critical business information online where it is accessible to employees, customers and partners, they require additional levels of security as well as flexibility," said Chris Christiansen, IDC analyst.
Today, a number of qualified vendors provide Encryption, Authentication,
Authorization, Audit, and Administration components, however, most significant
intrusions occur via exploitation of weaknesses in the operating system. What
has not been widely available or easy to implement is system-wide protection at
the operating system level. For example, hackers exploit operating system
weaknesses to gain root access, which they subsequently use to disable other
security measures. Historically, most attempts at providing operating system
level protection resulted in unacceptable performance trade-offs for most
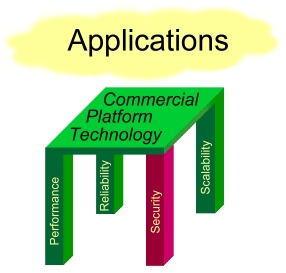
commercial applications. The challenge, as shown in Ffigure 1, has been to
provide fundamental security without impacting the other pillars of modern
systems, nor requiring changes to the applications.

Figure 1- Foundations of Secure Technology. Most
successful intrusions are through the holes in system security, giving hackers
access to the Root. Systems today are unable to cope with system level
hackers.
Agorics has developed the GuardOS technology to ensure system-wide security for application servers. the GuardOS platform has been designed to address the common limitations of most security systems by preventing the use of resources by viruses, Trojan horses, etc. It completely eliminates the need for patches and updates every time a new virus is discovered because viruses are stopped before they can impact the system. The GuardOS platform also uses the technology of "capabilities" to confine applications in customized protection domains. This use of capabilities enables provides an unprecedented level of security without impacting system performance.
The GuardOS Secure Operating System is a proprietary application server technology that allows Java and multiple Java Virtual Machines to host mission critical applications without the requirement of a traditional operating system. This means that Java applications running on the GuardOS platform are unquestionably secure, reliable and provide very high performance levels. The GuardOS platform provides a Java Virtual Machine interface for rapid application development, and strong support for native methods that leverage the security and reliability features of theGuardOS paltform. A typical general-purpose operating system runs millions of lines of code; by comparison, the GuardOS software is a trim 60,000 lines of code. This means fewer bugs; there is also no opportunity for hackers to compromise the system by gaining root access.
In today’s programming environment, Java Virtual Machines provide all the functionality that application developers require. This makes application servers running JVM’s the ideal platform for the GuardOS system (See Figure 2). In the GuardOS environment, Java applications will require no modification to run successfully; therefore, administration and manageability will not be adversely impacted.
|
Features |
GuardOS Architecture for JVM’s |
|
Secure, reliable compartmentalization of applications High availability, continuous operation in the presence of hardware failure "Fail Over" / Hot Standby and ultra fast restart capabilities Guarantees Quality of Service (QoS) High transaction performance |
|
Figure 2- Compared to a typical operating system environment the Trusted Computing Base (TCB) Portion of the GuardOS platform is very small.
Initially, the GuardOS system will be hosted on Sun Microsystems’ SPARC hardware, but it will be ported to other hardware platforms based upon market requirements. The GuardOS platform is a proven technology. Earlier versions of this proprietary technology have been in production and in service for mission critical applications in the financial community for many years. Agorics is currently porting and optimizing this patented technology for the Java application server market.
A key feature of the GuardOS technology in the support of Java-based business applications is the use of multiple, lightweight Java Virtual Machines. Without the burden of a large operating system, each application and even each client of an application uses a separate JVM. Communication between JVM’s is transparent to the application but is controlled by GuardOS security mechanisms.
The GuardOS technology provides a platform for mission critical requirements, allowing Java transaction applications to perform significantly better with less programming effort. This makes the GuardOS platform the ideal foundation for Internet and Intranet business applications and any other programs that require:
Using proven security concepts far beyond those found in traditional systems, the GuardOS engine allows operational patterns not conceivable elsewhere today. (See Table 1).
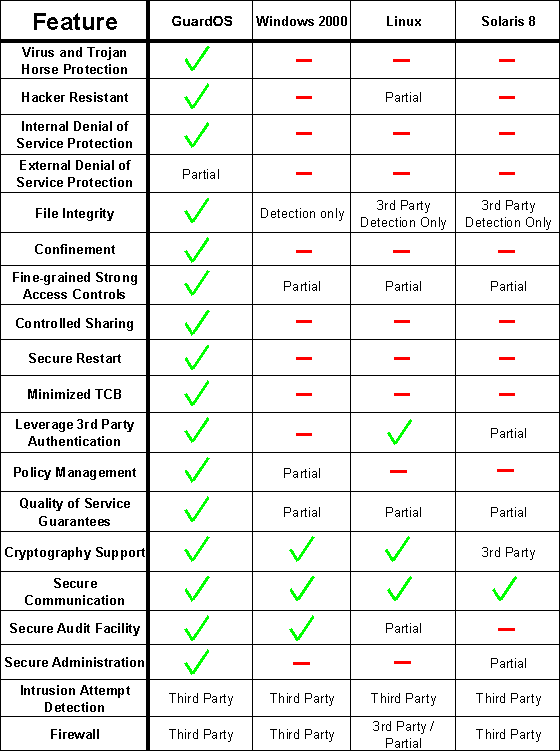
Table 1- Comparisons With Common Operating Systems
The GuardOS engine first provided a highly secure and reliable operating system for virtual machines hosted on the IBM 370, CMS operating system. It is based on original work done at Tymshare in 1975 by Ann Hardy’s development team, many of whom are Agorics’ developers. Even in those early days, the remote-computing sector recognized many of the issues now confronting the ASP industry. This operating system was developed to address security, availability, scalability and manageability issues. Tymshare hosted many mission critical applications in finance and reservation services with this system. When Tymshare was sold to McDonnell Douglas, Ann Hardy spun out the GuardOS technology and formed a new venture-backed company, Key Logic. The company continued to develop, port and distribute this technology.
Today, Agorics holds the patents to this technology and is in the process of porting the code base to a Sparc platform. Since the code base is written in "C" and is a relatively short 60,000 lines, the porting process is straight-forward. The team has successfully completed a Proof of Engineering Concept in Q1, 2001, and is currently porting the first application to the GuardOS platform on Sparc.
Patent: # US 4,584,639: Computer Security System
A capability based computer system includes means, called a factory, for allowing two domains to share resources in a secure manner. Factories are special domains which, in combination with corresponding kernel functions, allow a first domain (called a builder domain) to install a program and other components in a factory for use by other domains, and then to seal the factory, thereby leaving the builder domain with no keys to the factory except a special type of entry key called a requestor key. The holders of requestor keys can use the program in the factory by invoking the requestor key. This causes the factory to set up a new special domain for the requestor which allows the requestor to use the program in the factory to process data without being able to inspect the program. Further, the factory mechanism includes means for the requestor to confirm that the factory includes no keys which could compromise the confidentiality of the requestor's data.
Agorics is a leading eSecurity research and development organization
based in Los Altos, California. Formed in 1994 by noteworthy eSecurity
professionals, the company has authored ten patents in the information security
space. Agorics has been selected by leading organizations such as Sun, IBM, and
Charles Schwab to design and develop core information security
products.
[Home] [Agorics Technologies] [Tech Library]
Notice of Copyrighted Material:
Work
presented here is copyrighted material belonging to Agorics, Inc. (Copyright
© 2001 Agorics, Inc.) Agorics, Inc. reserves all copyrights. Agorics
disclaims any warranty as to the utility, accuracy or effectiveness of the
information contained in this document and specifically disclaims any liability
for consequential damages that may result directly or indirectly from use of
the information in this document.